The emergence of health assistants tailored for virtual support, like DocVA, has significantly changed the delivery of healthcare services. These…
Read More »Tech
Modern vehicles are increasingly equipped with sophisticated technology designed to enhance the driving experience. One such innovation is the infotainment…
Read More »In the dynamic world of social media, TikTok has emerged as a powerhouse platform, captivating millions of users worldwide. With…
Read More »The Snipping Tool is a versatile utility that enables users to capture, edit, and share screenshots effortlessly. Whether you’re documenting…
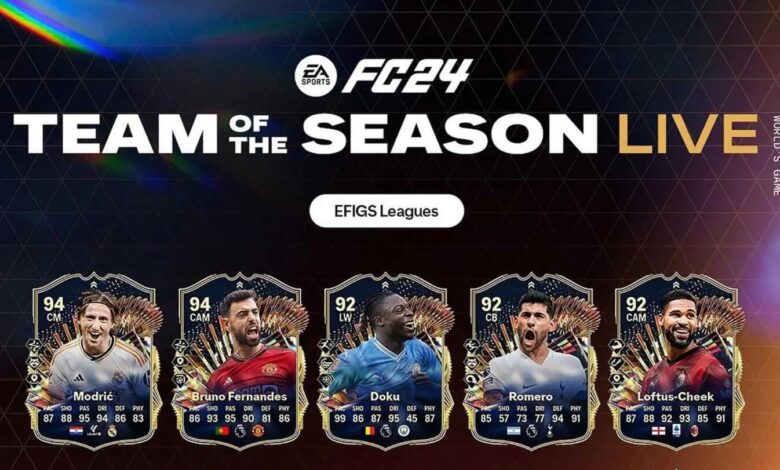
Read More »EA releases the 6th Team of the Season update, and with it come several new reasons to go back into…
Read More »In the digital age, the way we consume sports, especially football, has undergone a significant transformation. Gone are the days…
Read More »In an era where digital memories are cherished more than ever, MyGetPix com emerges as a beacon for photo enthusiasts…
Read More »In an era dominated by numbers and data, certain sequences catch our eye, sparking curiosity and intrigue. One such sequence…
Read More »In the bustling digital ecosystem of TikTok, where creativity meets virality, Geekzilla emerges as a beacon for tech enthusiasts and…
Read More »Tamil cinema, with its rich storytelling traditions and vibrant cultural tapestry, has captivated audiences both in India and around the…
Read More »